What is API Authentication and Why Is It Important
What is API Authentication and Why Is It Important?
In the realm of modern software development, ensuring secure and authorized access to APIs is paramount. API authentication is a fundamental aspect of this process, responsible for verifying the identity of the users or systems accessing the API. This article explores what API authentication is, its significance, common authentication methods, and practical examples of implementing these methods using EchoAPI.
What is API Authentication?
API authentication is the process of validating the identity of clients trying to access server resources via an API. It ensures that only authorized users or systems can interact with the API, safeguarding sensitive data and functionalities from unauthorized access.
The Significance and Role of API Authentication
Security: It prevents unauthorized access and protects sensitive data by ensuring that only legitimate users can access the API.
Accountability: By authenticating users, APIs can track user activity, offering a secure and accountable way to interact with the server.e server.
Access Control: Authentication allows for varying levels of access based on authenticated user roles or permissions.
Prevent Abuse: Protects the API from abuse, such as excessive usage or malicious activities, ensuring that the service remains reliable and performant.
Common API Authentication Methods
Here's an overview of several widely used API authentication methods:
| Authentication Method | Description | Use Cases |
| Basic | Uses a base64-encoded username and password | Simple authentication for non-critical applications |
| Bearer | Uses a token for authentication which is included in the request header | Common in OAuth implementations |
| JWT (JSON Web Token) | Token-based authentication with embedded user data | Stateless, scalable authentication for distributed systems |
| Digest | Uses a hash function to encrypt login credentials | More secure than basic, but less common in modern APIs |
| OAuth 1.0 | Older version of the OAuth protocol | Legacy systems that still use OAuth 1.0 |
| Hawk | Uses a cryptographic token for message integrity | Ensures message integrity and verification |
| Akamai | Uses Akamai EdgeGrid for authentication | Securing and scaling global web applications and APIs |
Comparing Common Authentication Methods
| Method | Ease of Implementation | Security Level | Stateless | Common Use Cases |
| Basic | Easy | Low | No | Simple, lightweight APIs |
| Bearer | Moderate | Medium | Yes | APIs needing token-based auth |
| JWT | Moderate | High | Yes | Distributed systems, microservices |
| Digest | Moderate | Medium | No | APIs needing improved security over basic |
| OAuth 1.0 | Complex | Medium | No | Legacy systems |
| Hawk | Moderate | High | Yes | APIs requiring message integrity |
| Akamai | Complex | High | Yes | Securing and scaling global platforms |
Practical Examples of Authentication Methods
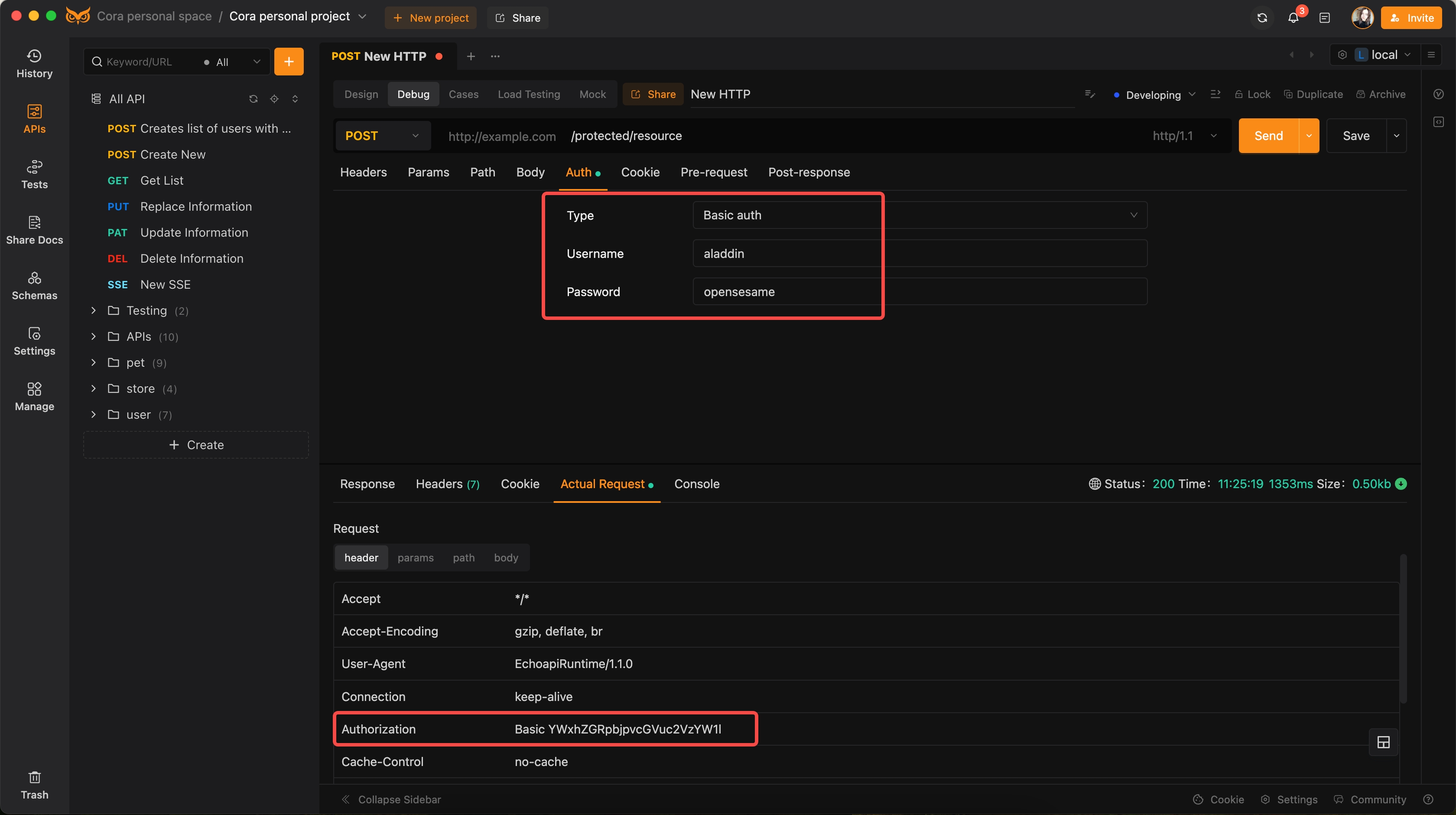
Example 1: Basic Authentication
Scenario: A client application needs to access a protected endpoint.
Code Snippet:
POST /protected/resource HTTP/1.1 Host: example.com Authorization: Basic YWxhZGRpbjpvcGVuc2VzYW1l
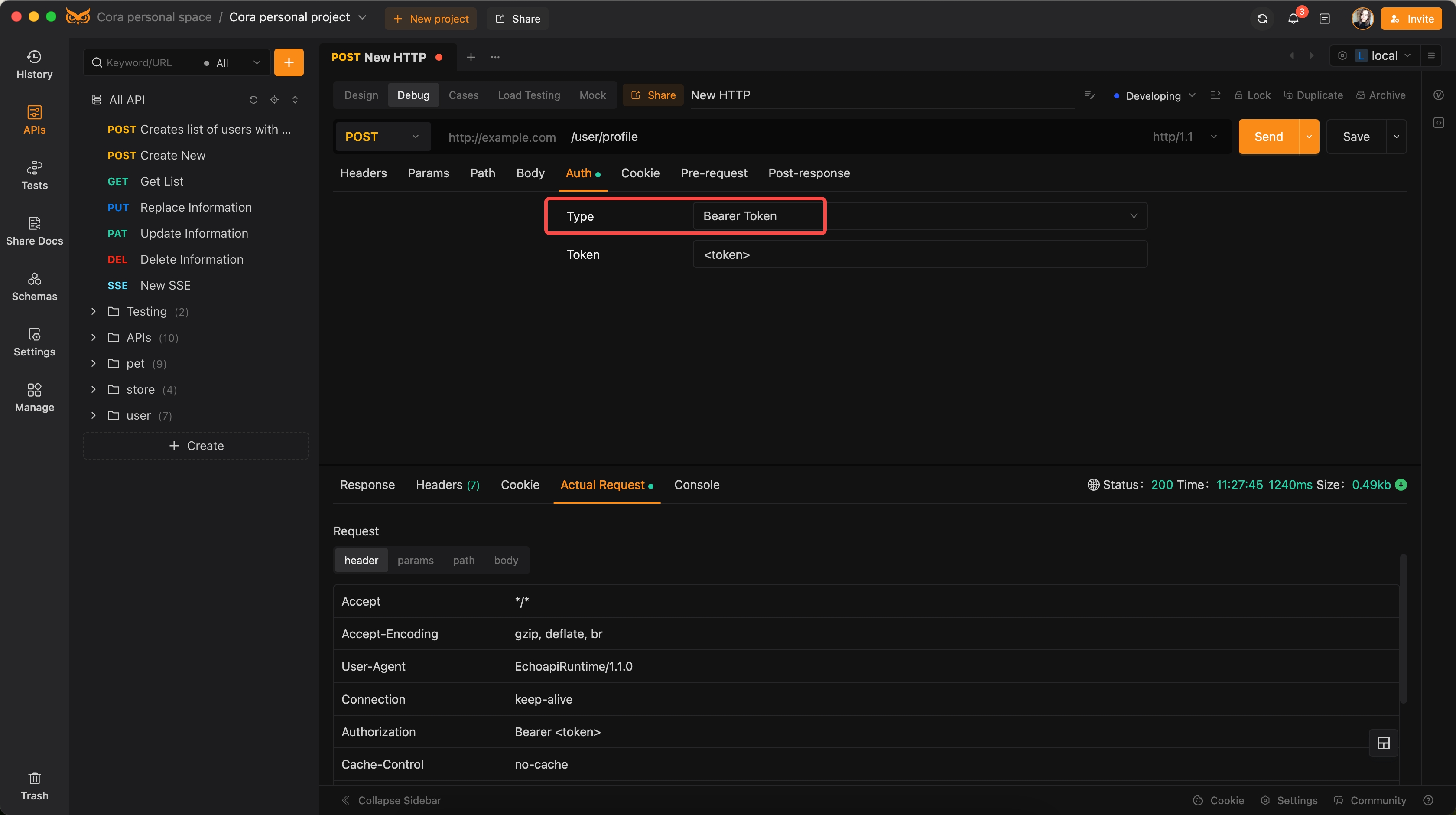
Example 2: Bearer Token Authentication
Scenario: Accessing an API endpoint with a Bearer Token.
Code Snippet:
POST /user/profile HTTP/1.1 Host: api.example.com Authorization: Bearer <token>
Example 3: JWT Authentication
Scenario: A client retrieves user information using a JWT token.
Code Snippet:
POST /api/user/info HTTP/1.1 Host: api.example.com Authorization: Bearer <jwt_token>
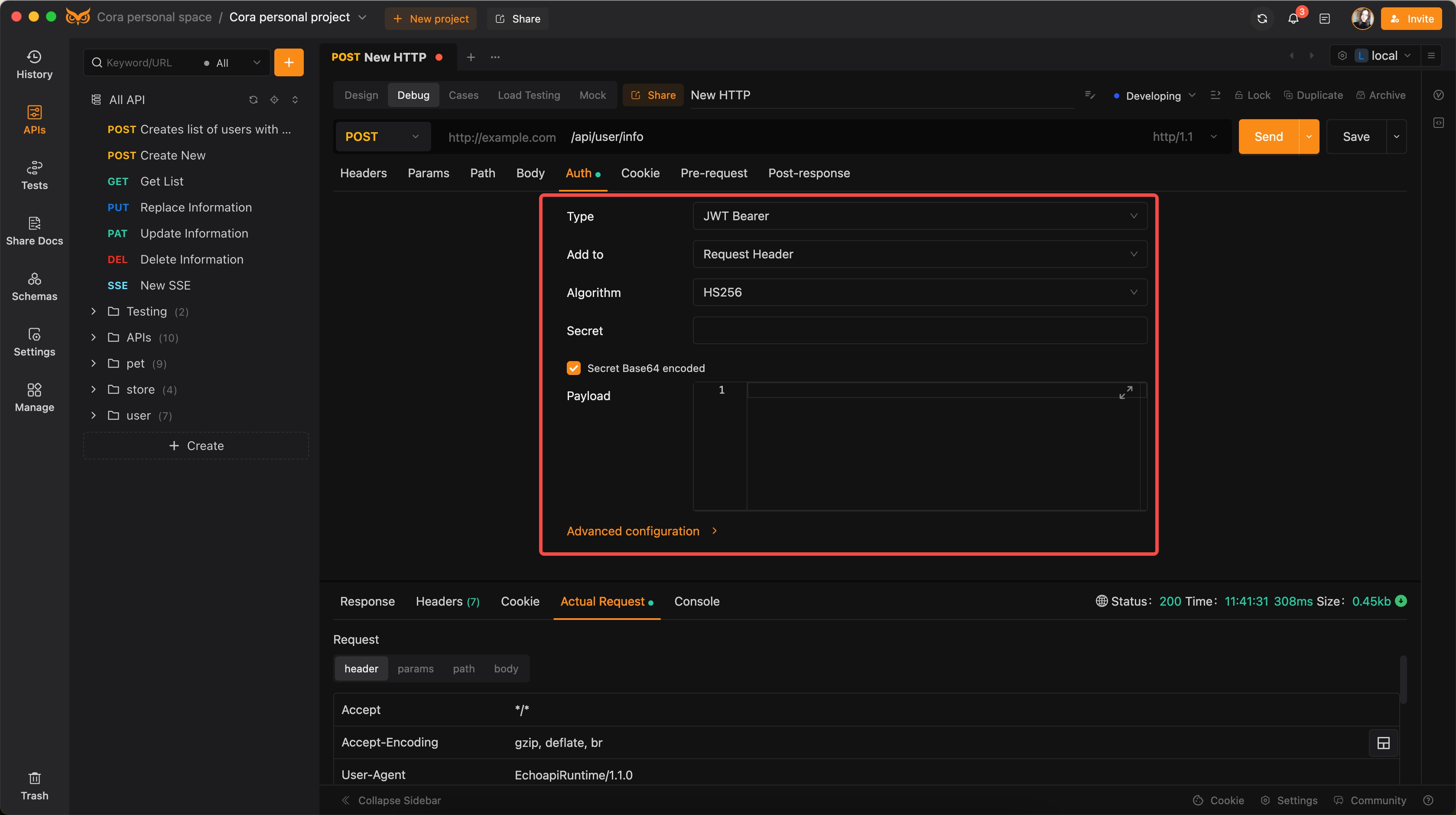
Using EchoAPI to Add and Test Authentication
EchoAPI simplifies managing and testing API authentication methods. Here’s how:
Create or Import a Request:
- Start by creating a new request or importing an existing one.

Set Up Authentication:
Navigate to the authentication section of the request setup.
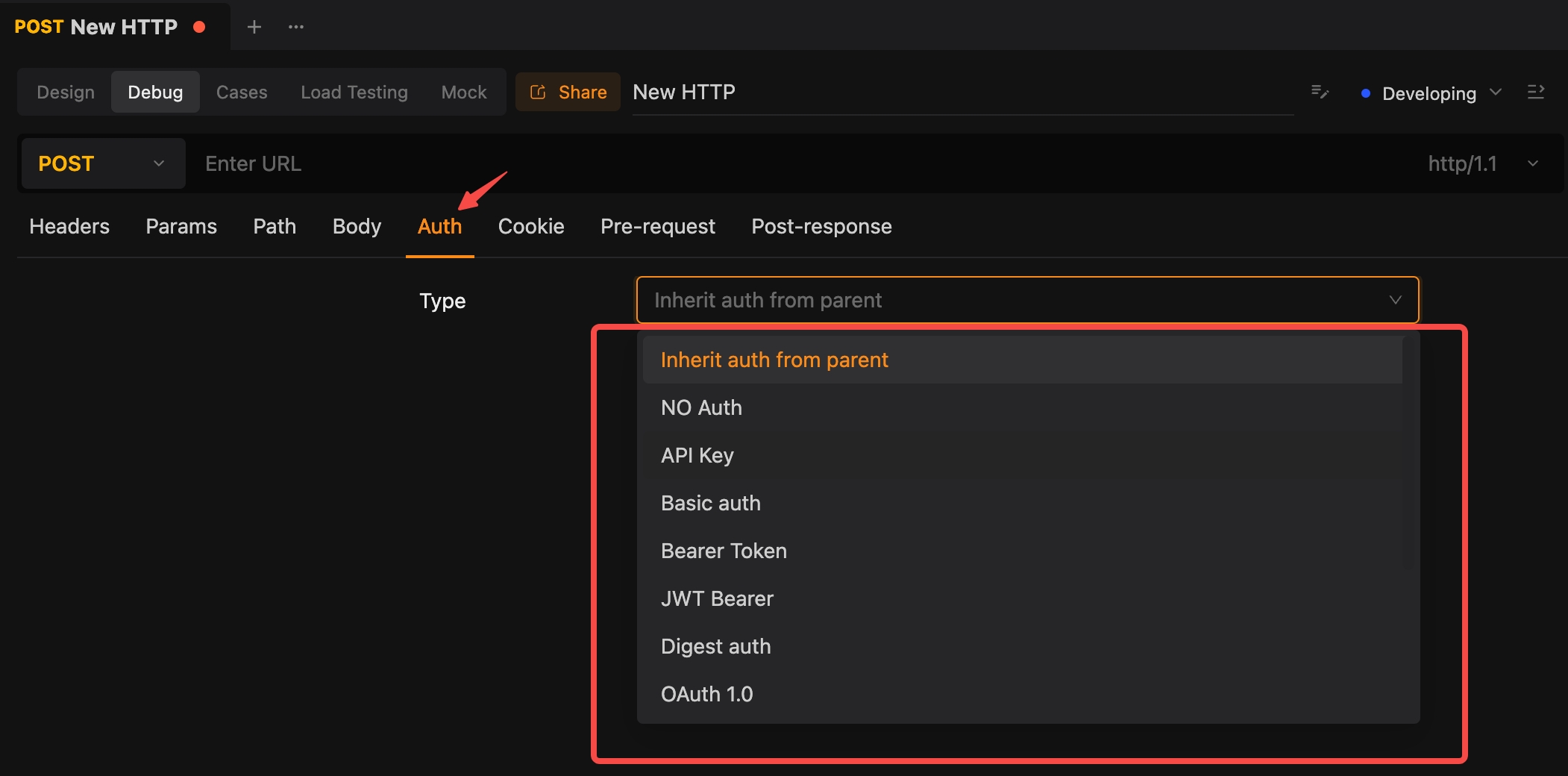
Choose the appropriate authentication type (e.g., Basic, Bearer, JWT).
Input necessary credentials or tokens.
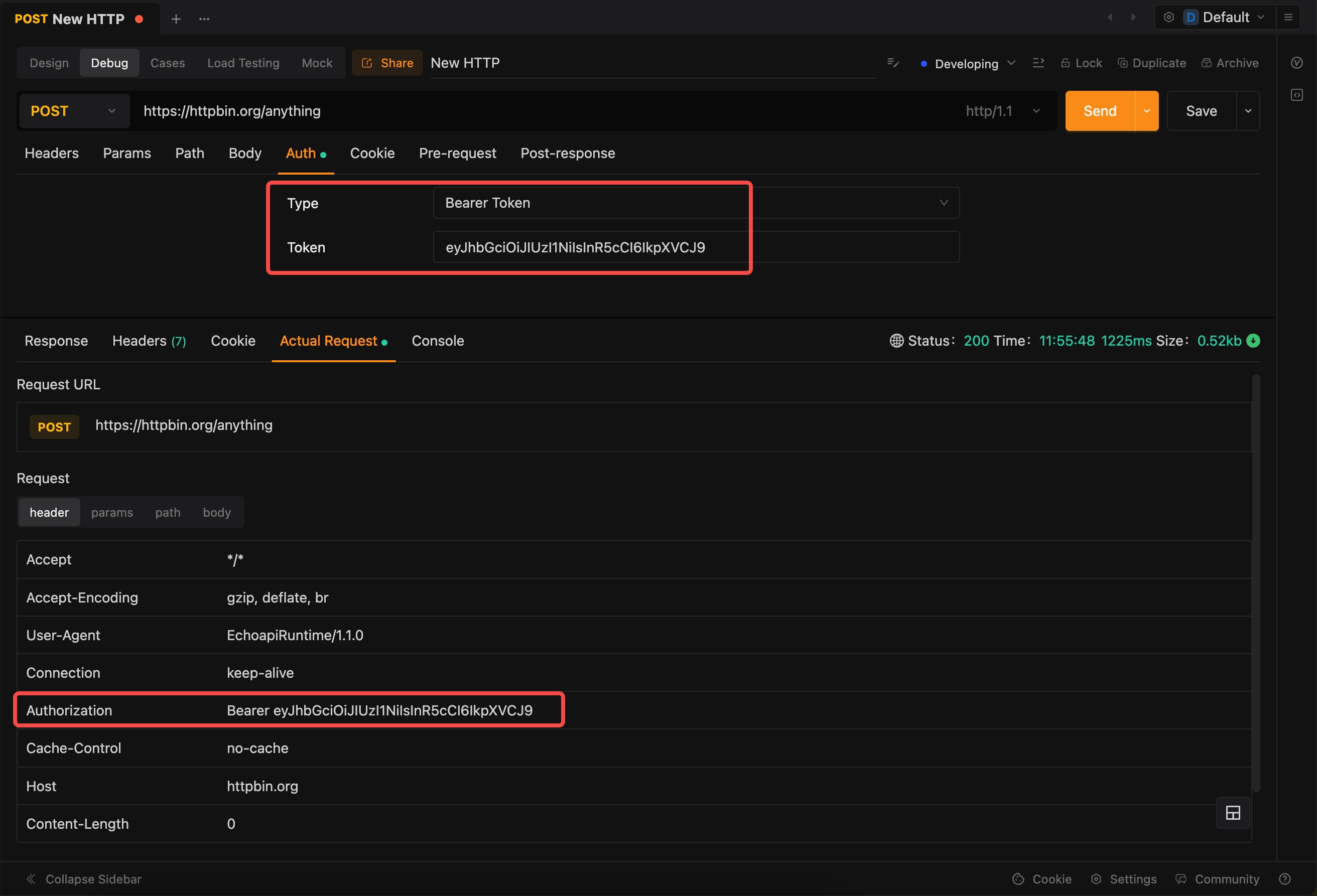
Executing Requests:
- Send the request and inspect the response to ensure that authentication is successful.
Conclusion
API authentication is a cornerstone of secure API design, ensuring that only authorized users or systems can access sensitive data and functionalities. Understanding and implementing various authentication methods—such as Basic, Bearer, JWT, and Hawk—helps developers enhance the security and reliability of their APIs. Tools like EchoAPI facilitate the process of testing and managing these authentication methods, making it easier to build robust and scalable applications. By mastering API authentication, developers can safeguard their systems and provide a secure user experience. 🔐🌐🚀
Try EchoAPI for VS Code today!